| Stay up to date with project news, upcoming events and results | Subscribe to Newsletter |
Technical Approach
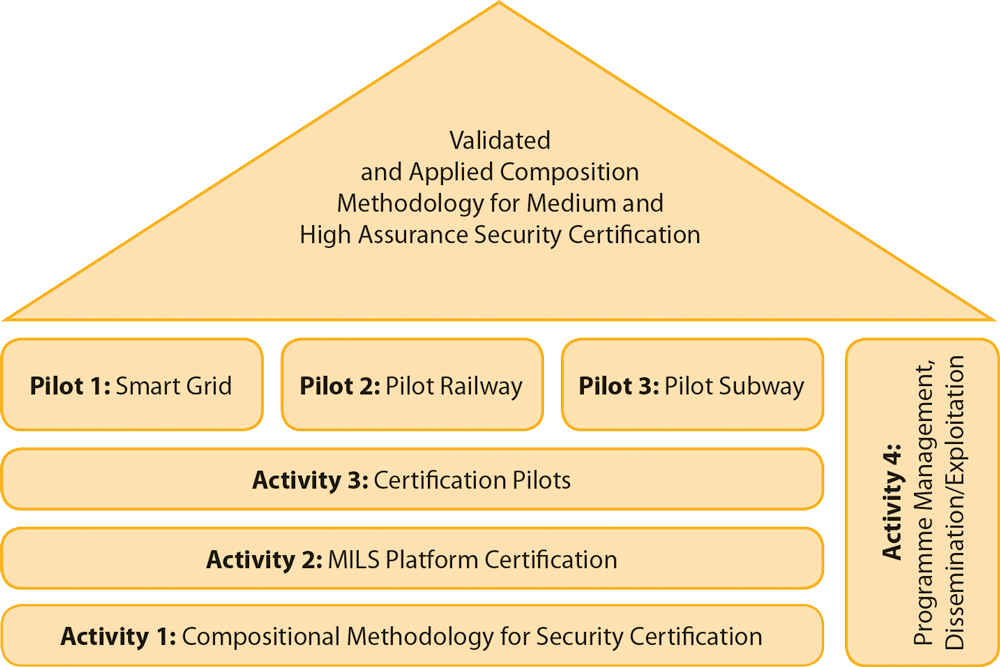
certMILS has three technical activity lines and one management activity structured into ten work packages (WP) in order to increase efficient information exchange. The total project duration is 48 months and every WP has its own objectives and interfaces aligned with the project's overall concept and goals.
Activity 1: Compositional Methodology for Security Certification
- WP1 "Baseline for compositional evaluation"
Partners with security and safety backgrounds summarized existing compositional security regulations/interpretations (D1.1), what tools/techniques exist (D1.2), how to do compositional certification for an SK-based product (D1.3).
- WP2 "Standardisation of MILS integration methodology"
We drafted the Base MILS Protection Profile (D2.1) using the Security Target (ST) and evaluated that it meets CC content requirements. We identified potential PP Modules that could be of use for the MILS community for additional functionality (D2.2). We edited the Base PP and PP Modules in parallel due to interdependency. We created templates for a security architecture (D2.3) and guidance for using an SK to build secure CPS systems (D2.4).
Activity 2: MILS Platform Certification
- WP3 "MILS platform definition"
This WP serves for the certification of an SK. It instantiates the more abstract WP2 work. We studied how the modular PP of WP2, consisting of a base PP and PP modules, represents this ST. We asked for certification body feedback.
- WP4 "MILS platform enhancement"
WP4 developed security testing methodology, considering the relevant standards CC and IEC 62443 and fuzzing to discover hard to find vulnerabilities (D4.1). We implemented a certifiable partitioned network driver with accelerators and described a certifiable MILS design of secure boot and update.
- WP5 "MILS platform certification"
WP5 provides assurance that the MILS SK works as specified in the ST. We reviewed product and development artefacts, including the ST itself, documentation related to the product life cycle, development and guidance and we produced CC evaluation reports.
Activity 3: Certification Pilots
The third Activity is divided into the three pilot WPs:
- WP6 "Pilot: Smart Grid"
For medium-assurance, a pilot was based on Industrial and Automation Control System (IACS) of an electrical substation, including Remote Terminal Units (RTU). We defined the security scope for the pilot, considering the standards IEC 62443 and CC. A master-slave configuration with control, communication and acquisition RTU devices was implemented. In order to scale the pilot from medium to high assurance, a compositional security design (with WP2 input) was made. We have ported the RTU architecture to PikeOS.
- WP7 "Pilot Railway"
A presentation of the use case demonstrator (security gateway) took place and the description of the use case of the railway pilot is done. Security requirements based on IEC 62443 for the railway pilot were defined and the pilot implemented.
- WP8 "Pilot Subway"
We specified the HW platform and operational environment of the demonstrator, defined SW components, which must be implemented to create application "T-compostion" and defined standards to show the principles and procedures for the implementation, acceptance and subsequent certification, and the pilot was implemented.
We are now doing a security evaluation of all three pilots according to IEC 62443.
Activity 3 integrates the pilots from existing and COTS components on the MILS platform and it provides the evaluation and certification results for Activity 1.
Activity 4: Management, dissemination and exploitation
- WP9 “Communication, standardisation, dissemination and exploitation”
WP9 obtains inputs from all other WPs and ensures the communication/ dissemination of results to the outside parties and participating entities. WP9 supports the partners to exploit the achieved results and impacts the European and international market. Results within each other WP will lead to contributions to standardisation activities, coordinated by this WP. We created a logo, templates and project colors to make certMILS recognisable in conferences, workshops and events. An IT infrastructure was set up, as well as a website, social media and Zenodo for public deliverables (https://zenodo.org/communities/mils/). We validated our SK protection profile approach by soliciting feedback from SK experts (D9.2). The consortium has already organized 3 MILS workshops with proceedings at Zenodo, published 16 papers and 5 newsletters.
- WP10 “Project, risk and innovation management”
The last WP draws from the input of all other WPs to ensure a successful project with respect to risk and innovation management. The management WP shows dependencies to all other WPs, ensuring that the tasks are in line with the project work plan in order to reach the common goals of certMILS. Kick-off, technical and advisory board meetings are taking place regularly and monthly telcos are held. Risk assessment is continuously performed as well.

